The Unseen Threat: Social Engineering
Most cyberattacks begin not with sophisticated hacks, but with straightforward social engineering tactics. Data shows that 87% of initial access vectors are a result of social engineering, primarily through phishing, malicious attachments, and fraudulent URLs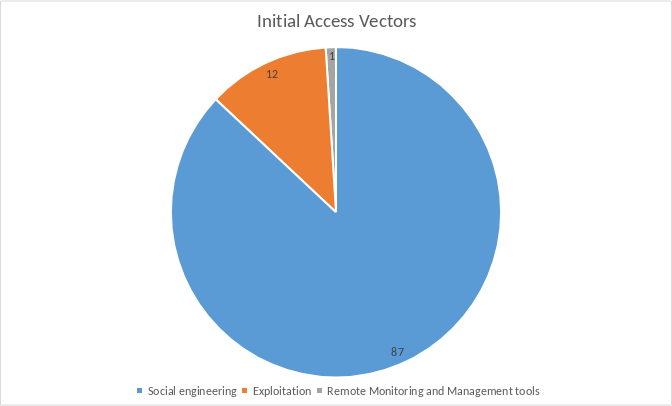
Initial Access Vectors
Misguided Investments
While the industry often focuses on the latest trends and shiny new security tools, weaknesses in email and collaboration platforms are often overlooked. This leads to misinvestments and a false sense of security, as companies pour resources into high-tech defenses while leaving their most vulnerable point—their people—exposed.
The Problem with “Shelfware”
Many enterprises already have the solution at their fingertips; they have done vendor vetting and procurrement alredy. Licensing bundles for Microsoft 365 often include security features such as Defender for Office 365 or, at the very least, Exchange Online Protection. These services provide functional layers of defense, including anti-phishing, anti-malware, and safe links/attachments, which can significantly mitigate these risks.
However, without proper configuration, these features are nothing more than expensive shelfware.
Beyond Security: Boosting ROI and Productivity
Activating and properly configuring these security tools not only improves your security posture and ROI for already purchased tools but also boosts productivity and reduces the time your IT team spends on incident response. It’s time to stop chasing trends and start securing what matter.