IDC EDR 2025
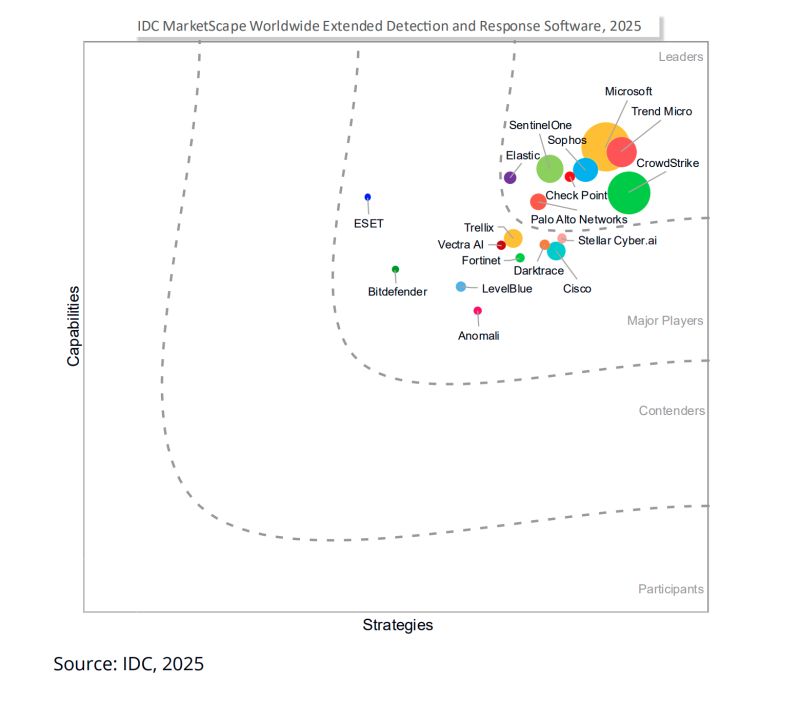
In most enterprises, security is a cost center, and businesses can’t afford to be bogged down by complexity and bespoke integrations. The advantage lies with the well-integrated platform, which reallocates resources and delivers tangible outcomes. Microsoft is positioned in the Leaders category in the 2025 IDC MarketScape for enterprise XDR software because it gets this right by focusing on native integration and operational efficiency.
From Complexity to Commodity
- Lowering the Barrier to Entry: Integrated platforms are important for improving the efficiency of both entry-level analysts and seasoned cybersecurity experts. Microsoft Defender XDR supports KQL but also offers a simplified UI-based, guided experience that automatically creates the queries for novice analysts. This moves security away from being a constant, bespoke development project dependent on scarce expert resources.
- Aligning Resources to Core Business: By choosing a cohesive platform instead of a siloed collection of tools, you reduce XDR adoption’s biggest challenges: budget and deployment complexity. This allows you to direct valuable, highly skilled staff toward core business initiatives, instead of maintaining complex, undifferentiated infrastructure in secondary domains.
The Advantage of Pre-Integration
- Rapid Operationalization: Microsoft is winning because its unified SecOps platform includes native offerings across the enterprise. If customers begin with Microsoft EDR, shifting to XDR is straightforward. This pre-integration helps you get started much faster than working to deeply integrate third-party tools.
- Risk Context: This comprehensive approach provides context to reduce the blast surface and produce high-fidelity alerts. Microsoft XDR’s highly-rated capabilities include correlating risk monitoring across all four security planes (identities, data, devices, and applications), which produces impact-based, risk-aware alert prioritization.
Value Realization is The New Chalange
With the integration battle won, companies now face a new challenge: operationalizing and extracting maximum value from the investment. Buyers should first clarify the total cost, including what is covered in a license, the compute cost for Copilots, and storage optimization strategies. They must then adjust the operating model to use insights across the organization. Without this, even the best platform becomes expensive shelfware.
See also my reflection on Worldwide Modern Endpoint Security Market Shares, 2024